On September 8, 2025, the open-source ecosystem was rocked by a massive supply chain attack. Popular npm packages like debug (357M+ weekly downloads) and chalk (299M+ weekly downloads) were compromised alongside 16 other libraries. The injected malicious code silently intercepted crypto transactions in browsers, redirecting funds to attacker-controlled accounts.
The sheer popularity of these libraries highlights a reality we don’t like to acknowledge because it means we have to do something about it: modern software development is only as secure as its weakest dependency. The way we build today, more like lego blocks and less hand crafting something means, if there’s a compromise, we all are affected.
What Are Packages and How Do Developers Use Them?
In the JavaScript ecosystem, a package is a reusable piece of code distributed via npm (Node Package Manager). Developers install them with commands like:
npm install chalk
The package gets added to the project's node_modules folder and listed in package.json. From there, developers import it into their code:
const chalk = require('chalk');
console.log(chalk.green('Success!'));
Packages often depend on other packages, forming a vast dependency tree. A single compromise can silently affect thousands of projects downstream. Cue this infamous image

How the Attack Happened
The attackers injected malicious code into the npm registry for these packages. Developers unknowingly downloaded the compromised versions, built applications with them, and pushed those apps to production. End users—and their crypto wallets—were the ultimate victims.
The Attackers then targeted the Maintainer by a phishing email requesting 2FA to be updated.
“The maintainer shared that he was compromised by the use of phishing, using this email coming from support [at] npmjs [dot] help : “
This wasn’t a one-off event. 2025 has seen multiple npm supply chain attacks, from Nx packages to eslint-config-prettier, exposing a growing trend: attackers increasingly target the software supply chain itself rather than individual systems.
Attack Flow Diagram:

[npm Registry] --(Compromised Package)--> [Developer's Project] --(Build)--> [Application] --> [End Users]
The red arrow highlights the initial compromise point when attackers publish malicious code to the npm registry, impacting everyone downstream.
What to do TODAY:
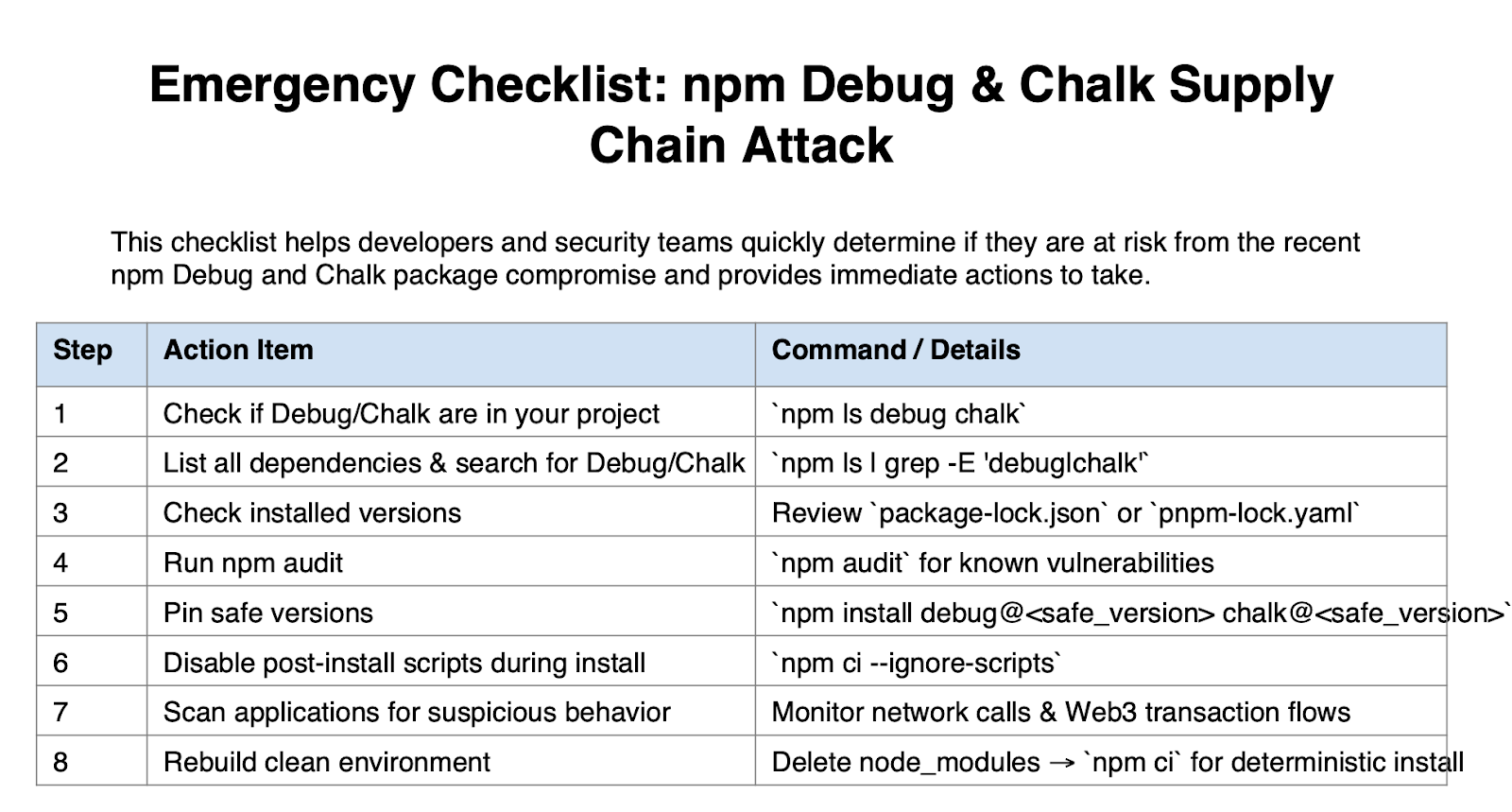
Impacted Packages (examples)
- ansi-styles@6.2.2
- debug@4.4.2
- chalk@5.6.1
- supports-color@10.2.1
- strip-ansi@7.1.1
If compromised versions are found: Immediate Actions for Developers
- Pin safe package versions to prevent pulling malicious updates.
- Rebuild and redeploy your apps from trusted, clean artifacts.
- Rotate secrets (API keys, tokens) and review wallets or transactions for suspicious activity.
Security Controls to Prevent Future Attacks
The good news? There are concrete steps teams can take to protect against this threat, and a reminder to all, question any request that has you updating your password. Phishing is still the oldest trick in the book that still works.
1. Package Security Controls
- Pin Dependencies: Use exact versions (e.g., 5.0.1 instead of ^5.0.0) to prevent automatic updates to malicious releases.
- Verify Integrity: Use npm audit, signed packages, or tools like Sigstore to ensure authenticity.
- Check Provenance: Trust packages with transparent security practices and verified maintainers.
2. Pre-Install Scanning & CI/CD Integration
- Static Analysis: Scan packages for malicious scripts before installation.
- Safe-Chain Tools: Wrap package managers with security layers that block risky packages.
- CI/CD Policies: Reject builds with unverified or abnormal dependencies.
3. Runtime Monitoring & Behavior Analysis
- Monitor Post-Install Scripts: Detect unexpected code execution after installing packages.
- Network Alerts: Flag unusual outbound traffic from build systems or applications.
4. Supply Chain Hygiene
- Reduce Dependencies: Use only actively maintained, necessary packages.
- Package Health Metrics: Prioritize libraries with frequent updates and multiple maintainers.
- Third-Party Risk Reviews: Treat dependencies like vendors: assess risk before adoption.
5. Web3-Specific Protections
- Transaction Whitelisting: Add multi-factor checks for sensitive crypto operations.
- Wallet Monitoring: Detect suspicious or unauthorized transaction patterns.
6. Organizational Measures
- Maintain an SBOM: Track all dependencies and versions.
- Vulnerability Disclosure Policies: Encourage fast, responsible reporting.
- Developer Security Training: Educate teams about malicious dependencies and phishing attacks.
The Takeaway
This is just the beginning. We know with Agentic attacks, hitting more targets at once is going to grow. Hitting sources that are trusted, widespread and often buried in builds means open source packages can become a lucrative target. The npm debug/chalk incident underscores that supply chain security is application security. Modern software relies on hundreds of dependencies. A single compromised package can put businesses, users, and entire ecosystems at risk.
By combining technical defenses (scanning, monitoring, version pinning) with organizational practices (SBOMs, training, disclosure policies), teams can build resilience against this growing threat.
Good Resources:
https://www.aikido.dev/blog/npm-debug-and-chalk-packages-compromised

.webp)
.png)
